
Two-factor authentication is the way to go for HIPAA compliance but what’s the best 2FA option for you?
What’s the best way to comply to HIPAA password requirements? Adopt two-factor authentication (2FA). In fact, HIPAA Journal states that 2FA is “the best way to comply with the HIPAA password requirements”.
The threat of data breach for healthcare data is showing no signs of diminishing, in fact quite the opposite judging by the HIPAA Journal’s June 2021 Healthcare Data Breach Report.
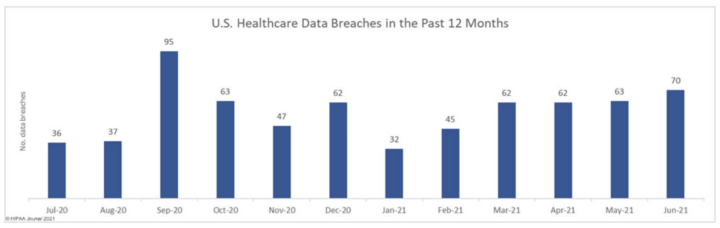
As the chart shows, breaches of 500 records or more in June increased by 11% from May and represents the highest volume of breaches since September 20.
The majority of these breaches were from phishing and ransomware attacks but the real impact here is on the 81,764 individuals whose Electronic Protected Health Information (ePHI) was breached.
2FA is not a universal shield against the threat of data breach, however the right solution significantly steps up defences and mitigates against the primary risk of breach – weak or stolen passwords, which account for the cause of more than 81% of data breaches.
What’s the best 2FA solution for me?
There is a multitude of vendors on the market promising to be the solution to your 2FA needs but where do you start?
Firstly, we recommend taking a step back and looking at the authentication universe. The authentication pyramid is an excellent place to start. Here you can get an understanding on the authentication slice of the Identity and Access Management (IAM) landscape. Is a one-time password (OTP) solution sufficient? How about push notifications to mobile, FIDO (Faster Identity Online), or public key infrastructure (PKI)?
HIPAA do recommend 2FA but they do not legislate any one particular method, and so it is up to IT leaders at healthcare organisations to navigate the different solutions and define the best option for their organisation.
In most healthcare organisations there is not a one size fits all approach. Typically, healthcare providers look to adopt the strongest method of authentication across their employees, particularly professionals accessing ePHI. However, this can be challenging to roll out across 100 per cent of the workforce. Use cases involving 2FA for shared devices, or 2FA for healthcare professionals working in the community can result in many solutions falling short.
Why PKI and FIDO presents an excellent 2FA solution for HIPAA compliance
Until recently MFA options have been binary, you choose one and try to make that work as best as possible, often leading to compromise on security or user experience. That is no longer the case.
With credential management software like MyID, healthcare providers are presented with a system to issue and manage PKI and FIDO based credentials from one pane of glass.
Both cryptographic based, PKI and FIDO present strong authentication that is in line with NIST levels of digital identity assurance. PKI has long been certified for federal agency use in line with FIPS 201 legislation and FIDO is also expected to be included in the latest FIPS 201-3 legislation, once ratified in late 2021.
Unparalleled MFA security
With PKI healthcare providers have the scope to not only utilise the strongest form of MFA but also enable employees to digitally sign documents and encrypt emails, providing a secure and auditable means of managing PHI.
With FIDO healthcare providers also have a cryptographic protected method of strong MFA but without the requirement for the infrastructure of a PKI solution (no certificate authority required). FIDO is simple to issue universally, not only across employees but also contractors and suppliers where necessary.
With leading credential management software, you will have a solution that can issue and manage PKI and FIDO across a wide variety of end user devices; smart cards, YubiKey, Feitian, and Thales security keys, iOS and Android mobile and tablet devices, and many other technologies.
User experience without compromise
All too often security and UX are seemingly incompatible but that doesn’t have to be the case. A good credential management system will allow administrators and operators to manage usage in line with security policy while also ensuring a good UX is delivered across the different user groups which employees have.
Roles based access ensures that security demands are fit for purpose and never overly cumbersome. A vendor neutral system will also provide the flexibility to issue credentials across the devices you want to use. Don’t be locked-in to a specific smart card manufacturer or unable to use a mixture of iOS and Android mobile and tablet devices as well as security tokens such as the YubiKey. The right system helps IT teams deliver a system that works across diverse user groups and provides the right UX for porters through to physicians, community support nurses through to operational therapists.
Contact us using Demo Request button at the top of the page and discover what MyID credential management will do for your organisation’s 2FA offering.
Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you
will find Intercede. Whether its citizen
data, aerospace and defence systems, high-value financial transactions,
intellectual property or air traffic control, we are proud that many leading
organisations around the world choose Intercede solutions to protect themselves
against data breach, comply with regulations and ensure business continuity.

