MyID SecureVault
Generate and Securely Store Cryptographic Keys
Securely storing, managing and being able to distribute cryptographic keys associated with certificates is an
increasing problem for many organisations. Often these keys are locked into certificate authority infrastructures, leaving the organisation locked into a specific vendor's products to access them even after the certificate authority is no longer in use.
MyID SecureVault provides a dedicated, CA independent and cryptographically protected environment for these purposes, offering integration capabilities with MyID CMS as well as vendor independent APIs to access the keys.
MyID CMS provides certificate import and storage, allowing retrospective recovery of the certificate and keys to end user devices.
Integration with MyID SecureVault provides a separate, secure database for storing keys imported from a legacy certificate authority.
The solution helps you
- Become independent of Certificate Authority vendors, allowing you to permanently take control of your
escrowed keys - Migrate key escrow from legacy certificate authority providers when they close down services, or you decide to switch CA vendor
- Provide a single, central store for key escrow where you have multiple certificate authorities from different vendors in use
- Provide secure key generation and protection services using accredited FIPS140-2/FIPS140-3 level 3 cryptographic modules
- Control access to these keys and monitor key management activities
- Achieve regulatory compliance by virtue of a well-defined perimeter and API
When used with the MyID CMS, this provides highly secure and controlled access to generate and retrieve keys escrowed for recovery on to a wide variety of devices including FIPS compliant security keys and smartcards, TPM protected computers, Mobile devices and software key stores.
Flexible options
The solution is based around modern database platforms, allowing your choice of deployment options to suit your security profile – on premise with Microsoft SQL Server, or in cloud platforms including Microsoft SQL Azure and Amazon AWS RDS SQL server.
The vault is simple to deploy providing flexibility of choice of cloud or on-premise installation and the ability to support high transaction volumes in load-balanced environments.
Hardware security modules provide the cryptographic root of trust in the solution. MyID SecureVault integrates with on-premise and cloud HSM services from Thales and Entrust.
SecureVault in Use
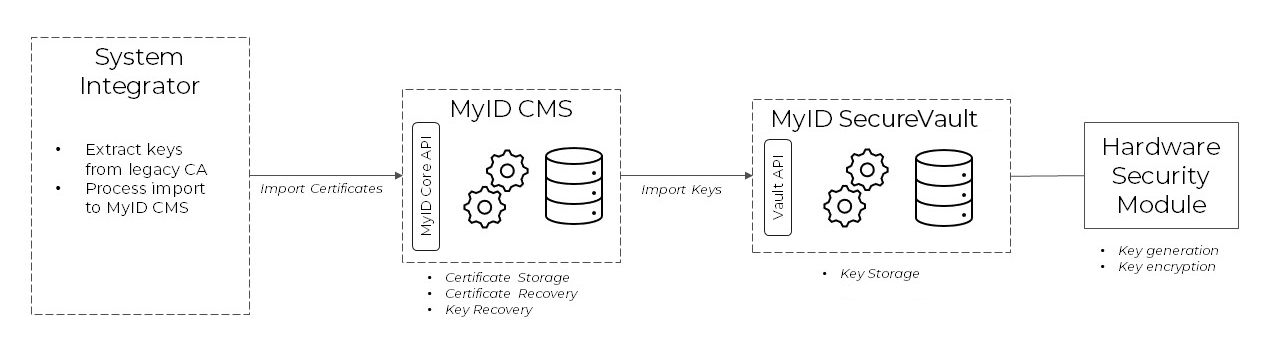
When a new archived certificate is issued, MyID CMS will interact with the SecureVault to trigger key generation. When an HSM is connected to the vault, key generation takes place on the HSM.
The private key is securely stored in the vault, and the public key used with the certificate request submitted to the certificate authority. The private key and certificate are then securely recovered to the end users device.
When a later key recovery request is created, the key is exported from the secure vault and recovered to the device along with the certificate. Key recovery processes are controlled by MyID CMS.
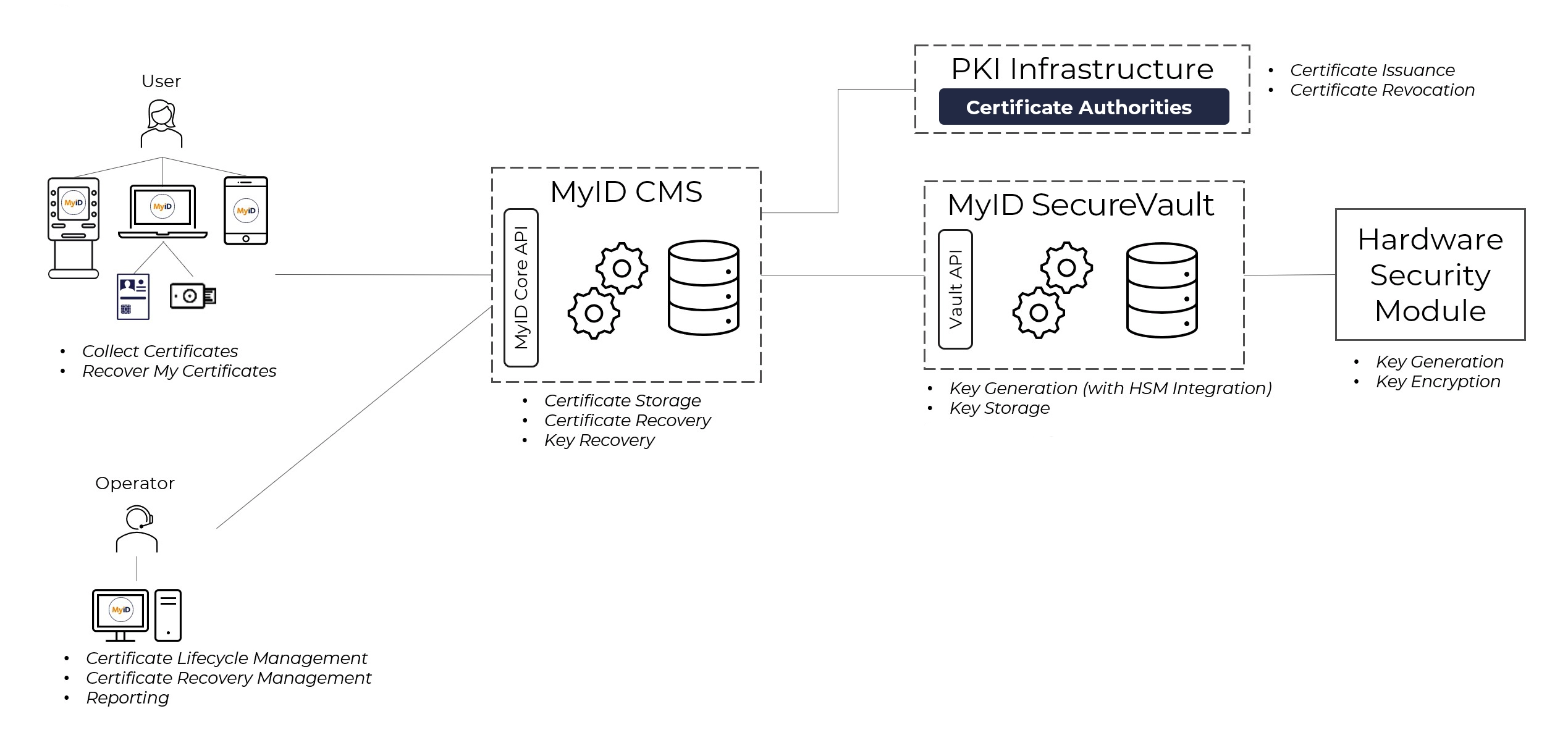
Built for systems integration & management
MyID SecureVault is built with an API first approach, to integrate with modern IT Service Management platforms as well as the MyID CMS. RESTful APIs, protected by TLS and strong authentication enable access to store, generate and recover cryptographic keys independently of the certificate authority.
How secure is this?
All sensitive information in the system is encrypted at rest and protected using keys held in the connected HSM. Use of FIPS-140 certified HSMs means the solution is based on the highest security standards at its core.
The CMS enforces role-based access control for key generation and recovery operations, providing separation of duties with strong authentication for access.
Download MyID SecureVault Data Sheet
Frequently Asked Questions
Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you will find Intercede. Whether its citizen data, aerospace and defense systems, high-value financial transactions, intellectual property or air traffic control, we are proud that many leading organizations around the world choose Intercede solutions to protect themselves against data breach, comply with regulations and ensure business continuity.


