Securing workforce login with biometrics – what IT leaders need to know
There was a time, not so long ago, when biometric technology was a thing of science fiction. As costs reduced and more innovations became commercially viable, we started to see biometric security systems rolled out more widely. First in areas like defence and law enforcement, then in more day-to-day environments like our workplaces and libraries.
Today, the technologies are vastly different, but they are almost ubiquitous. Most of the modern smartphones sold today incorporate at least one form of biometric ID technology – whether fingerprint, or facial recognition.
But now the technology is so common, the increasingly security and privacy conscious public is imposing new scrutiny. In fact, following pressure from groups such as Big Brother Watch, regulators are beginning to question the efficacy of some biometric technologies. In consumer applications we see regular reports that everything from photos to siblings can unlock mobile devices via facial recognition.
With fresh questions surrounding biometric identity verification technologies, businesses are looking to their security systems and wondering whether they are suitably protected against the threats the modern world poses.
Bearing Closer Scrutiny
It should come as no surprise then that the identity and access management (IAM) market continues to grow significantly, with research bodies predicting an annual growth rate somewhere between 13 per cent and 26 per cent.
Our modern businesses generate, process, evaluate and store increasingly large amounts of data. As this data has grown, so too has its value and the interest from malicious actors to obtain it. Not only has the inherent value of the data increased, the number of ways to try to nefariously access it has too.
Attack surfaces have been growing exponentially since we migrated paper records to digital data. As we connected more and more systems to networks, those networks to the internet, and technology advanced to the point where internet speeds and computing mobility meant employees didn’t have to work solely in the office, but could log on anywhere and everywhere – from their homes to their holidays – hackers have had more and more options to choose from to obtain unauthorised access to this valuable data.
It has never been more important for IT leaders from organisations of all shapes and sizes to protect the data they hold and yet many employees are still able to access secure data remotely with as little as a password. But with 81% of data breaches caused by compromised, weak, and reused passwords it is clear that these alone provide inadequate security for most corporate needs.
It is critical that organisations have more sophisticated solutions in place to ensure that only the right people have access to the data they hold.
In 2020 and beyond, businesses should be looking at far stronger methods of authenticating access to their systems and managing credentials of their employees.
Verifying Identity and Authorising Access
Biometric authentication is all around us. Indeed there are over 1.2 billion e-passports in circulation today – meaning over 1.2 billion travellers have a standardised digital portrait in a secure document to cross compare with live images at check-in gates around the world.
And while biometric technology is now very much a thing most members of the public recognise and understand in a consumer context, the concerns around things like privacy and efficacy we see there don’t seem to have filtered through to the workplace, where some are still using older and quite clumsy biometric technologies to authenticate the identity of employees and allow them to access physical space or online networks.
Anyone who has watched a police procedural will recognise the ease with which a fingerprint can be matched with a database of records to confirm an identity. So much so that even a layperson knows that thumbprints and fingerprints can be easily used to identify an individual. Unfortunately, that’s given rise to a perception that if data can only be accessed with a verified thumbprint, it’s secure. As we are all too well aware, that’s not quite correct.
Today’s innovative technologies have penetrated society almost completely in the most developed markets, with a large majority of the adult population carrying sophisticated computing devices in the form of smartphones on their person, throughout their work and home lives. A significant number of these support biometrics of some sort and provide a relatively simple and frictionless user experience. That may be enough to justify unlocking a phone to a menu screen, but is it enough to allow access on to a corporate IT network?
Combining Technologies to Build Trust
Biometric technology – like any other – has its disadvantages. In the world of identity and access management, centralised biometrics can still be compromised just like any ‘shared secret’. For IT policies demanding high security environments, the platform security of a biometric device may not be of the required strength.
That’s not to say that biometrics don’t have a role to play in delivering secure network or physical access. By itself, a biometric match is still just a single factor of authentication. Combining biometrics with other authentication methods in a multi-factor authentication (MFA) system is one way to retain ease of use, while making the security robust enough for the modern enterprise and the threats it is likely to be exposed to.
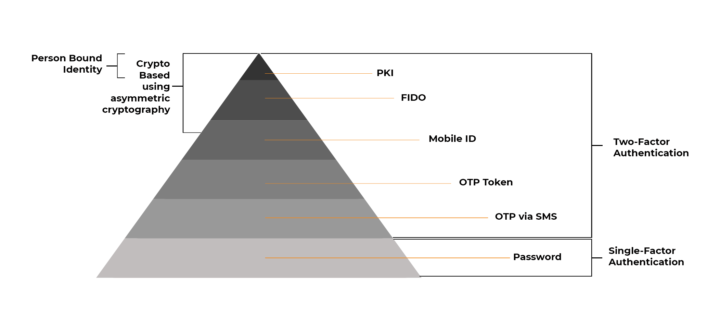
As an organisation, we champion strong authentication as standard and encourage CISOs to move towards the top of what we call the “authentication pyramid” wherever possible. But many are still convinced that strong authentication is reserved for big business and big budgets.
That is not the case, and we are working to raise awareness that strong authentication is achievable for organisations of all sizes.
This pyramid provides a simple way of visualising how the authentication slice of the IAM landscape breaks down and categorises the technologies that are currently available on the market.
Practical Solutions to IAM Problems
As the pyramid explains, in fewer words, moving up the pyramid, increasing the strength of authentication factors, and combining these strong factors of authentication into a single credential management system is an effective way of enhancing cybersecurity.
Employees will remain largely unfazed by strong multi-factor authentication, provided it is low friction and not subject to constant reiteration. Maintaining something easy to use without becoming burdensome is critical to a system’s success.
Until relatively recently, this was difficult to pull off in practice. In years gone by this kind of system was overcomplicated and cost prohibitive to deploy. Only those with the biggest concerns about unauthorised access to their databanks – militaries, law enforcement agencies, and defence firms – even thought about implementing them.
Thankfully engineers and technologists have been working on this problem, and have been able to innovate simpler and much more cost effective ways of managing the process of verifying the identity of those who wish to access networks, authorising that access, and managing the full lifecycle of those issued credentials – so that if a person’s status changes, their access can be reviewed, rewritten, or revoked.
Today, credential management systems that enable biometric factors of authentication to be combined with Fast ID Online (FIDO) or Public Key Infrastructure (PKI)-based authentication methods to provide a combined Multi-Factor Authentication (MFA) solution that is sufficiently convenient for employees, whilst retaining the security needed at an organisational level, all without excessive cost.
The Options Available
Like biometrics, these technologies have their strengths and weaknesses, and depending on the organisation and its needs, one may be more suitable than another.
FIDO, while growing in popularity, has its limitations. It does provide a secure digital identity, but not a person-bound digital identity, and as the public key is not directly bound to user identity, it is difficult to prove non-repudiation. This means that the authentication element is limited to login – a user cannot securely sign or encrypt without additional solutions.
PKI uses asymmetric cryptography, and once a user is enrolled, a certificate holding a public key and the identity of the person, is used to confirm that an authentication or signature performed by a private key is the correct key (i.e. belongs to the right person). In effect the certificate links the person with the private key without ever exposing the private key.
However, the legacy of this technology’s earlier years still persists, and there remains a reluctance among many IT leaders to moving to PKI-based credential management. Despite the obvious upsides in terms of its ability to verify who is trying to access what, there still exists a perception that the technology is too complex and expensive to roll out for most organisations.
As end user technologies, such as smartphones and USB tokens like the YubiKey, have provided more sophisticated security as standard, and pre-installed enterprise technology like Microsoft’s Windows Hello for Business, this type of crypto-level protection has become far more accessible for organisations of all sizes.
Solutions That Scale
Another hang up from yesteryear, has been that the kind of sophisticated MFA security technologies we’ve been exploring, have been difficult to manage at scale. But with the kind of growth and development we’ve seen in the business world in the past few decades, many of the businesses who are looking to deploy IAM solutions are large, global entities. They have outposts in many markets, and employees that follow the local norms in those markets. When procuring a security system such as this, they need something that works universally across the whole workforce – not just one satellite office.
Where previously managing credentials at volumes of anything above 500 employees was complex and hugely time consuming for IT teams, credential management software now makes this a relatively straightforward endeavour.
New systems that pair a convenient user experience for the employee with a unified central console that allows for the full lifecycle management of credentials for re-issuance, revocation, unlocking, renewing, removing and updating make the prospect of PKI-based identity and access management at scale commercially viable. Old concerns no longer apply in the same way.
Though there are some areas in which arguably more attention needs to be paid than in previous years. For instance, to local customs and available technologies. In a globalised society with multinational businesses the most sophisticated technology readily available in the market where the penetration of the latest technologies is lower, needs to be applied universally throughout the whole system to prevent a multi-tiered system where one market, be it through culture or technology present a more attractive target for malicious actors. The ability to integrate this technology – whatever it may be – into a solution that removes the complexities of managing PKI credentials makes the strongest form of user authentication so much more accessible for enterprises who don’t want to compromise on data security.
PKI-based credentialing can be executed today with relatively cost-effective USB tokens or even a smartphone app – binding a key to a user identity, and supporting existing security technologies within the business, such as PIN, fingerprint, or facial recognition. This additional step, matching something an employee has (the credentialed device) with something they know (a PIN) or something they are (biometric) allows the organisation to be confident that only those authorised to access a network/location are doing so. Much more so that any of the individual technologies in isolation.
Whether organisations want to issue staff with physical USB tokens or use an app that can be downloaded on to personal smartphones – there are a wide variety of ways they can provide the kind of security the modern workplace demands.
Constant Change
As technology advances, so too do the attempts to undermine it. Security technology continues to improve, but hackers’ ability to work around it does too. It is therefore incredibly important for organisations to continuously re-evaluate their systems, updating them regularly to maintain the necessary protections for their data.
For organisations that want a better way to protect their networks and data there is a rapidly growing market from which to select vendors and offerings. This is an encouraging sign for employees, citizens, consumers and wider society as we become increasingly security conscious about the digital world we live and work in.
Moving to credential management systems that enable strong methods of multi-factor authentication – including biometrics – to verify identity is easier and cheaper than it has ever been. It’s time that organisations look to the authentication pyramid when procuring these solutions, to select the most appropriate systems for them, that balance complexity, ease-of-use, of security to roll out up-to-date measures that protect their most valuable assets, intellectual property, and people.
Whether it’s to provide secure network logon, or access to a physical space, solutions are available that make it easy for enterprises of any size and structure to step up to the most secure method of multi-factor authentication across their workforce.
Want to understand how you can deploy biometric authentication across your workforce? Contact us now to find out more about the MyID software platform and arrange a demo.
Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you
will find Intercede. Whether its citizen
data, aerospace and defence systems, high-value financial transactions,
intellectual property or air traffic control, we are proud that many leading
organisations around the world choose Intercede solutions to protect themselves
against data breach, comply with regulations and ensure business continuity.