Understanding levels of assurance
With FIPS 201-3 approved, it is important to understand how the levels of assurance defined in the standard affect the authentication of federal agencies and its supply chain. Ensuring that those interacting with Government systems over open networks can be verified and validated, making sure you are meeting the criteria and are protected from cyber-attacks.
Authenticators are the cornerstone of authentication, and a digital identity will be authenticated based on three main factors.
- Something you know – i.e., a password or pin
- Something you have – perhaps an ID badge or Cryptographic Key
- Something you are – biometric data such as a fingerprint.
If you are using more than one factor, it is more commonly known as Multi-Factor Authentication (MFA) and the strength of the authentication is determined by the number of factors employed, the more factors used – the stronger the authentication system.
In the National Institute of Standards and Technology NIST SP800-63-3 – Digital identity Guidelines, there is more guidance on the levels of assurance.
The levels of assurance are split into three categories – Identity Assurance Level (IAL), Authenticator Assurance Level (AAL) and Federal Assurance Level (FAL), and each category now has 3 levels where 1 is the lowest and 3 is the highest form of assurance.
- Identity Assurance Level (IAL)
How applicants can prove their identities and become enrolled as valid subscriber within an identity system or credential management system.
- Authenticator Assurance Level (AAL)
A measure of the certainty that only the holder of the authenticator can perform the authentication. This measure covers the security of any device or secret, management of the authenticator and the strength of the authentication protocol. We discuss in more detail authenticator assurance level below.
- Federation Assurance Level (FAL)
What is the process between the relying party and the identity provider and potentially the federation authority?
Federated identity is a mechanism where multiple relying parties (e.g., applications) leverage an identity provider to authenticate end-users and return assertions (e.g., information about the end-user) back to the relying party.
FIPS201-3 makes the case for the use of federated identity to onboard additional applications to use strong authentication. FAL describes requirements for how assertions are constructed and secured for a given transaction.
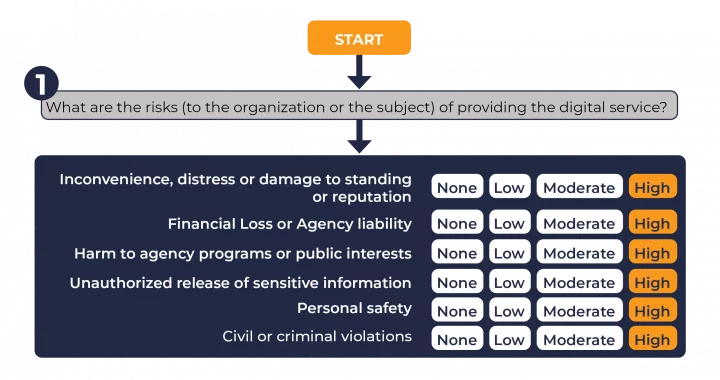
FIPS 201-3 does not stipulate that you need to use a specific software programme or system. But it does say that you need to fully understand the risks if protected information is lost, stolen or damaged and the consequences of a data breach.
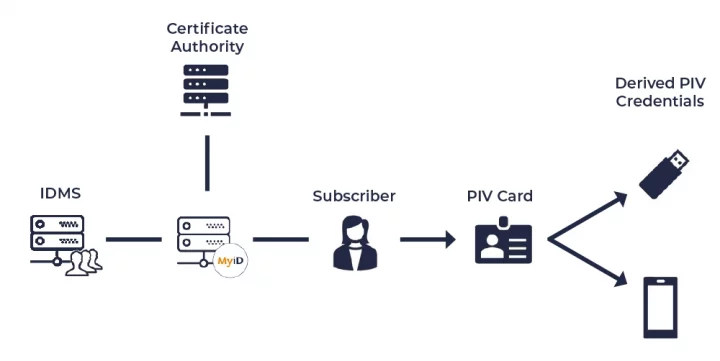
Derived Credentials
MyID® from Intercede can issue derived credentials with the extended range of form factors for authentication which are now permitted in FIPS201-3. A derived credential is an additional credential that can be derived from an existing credential (e.g., PIV card). At the point of issuing the derived credential, rather than repeating the expensive process of issuing an identity, but with the assurance that the identity proofing is given, authenticating with the original credential.
How can you comply with the FIPS201-3
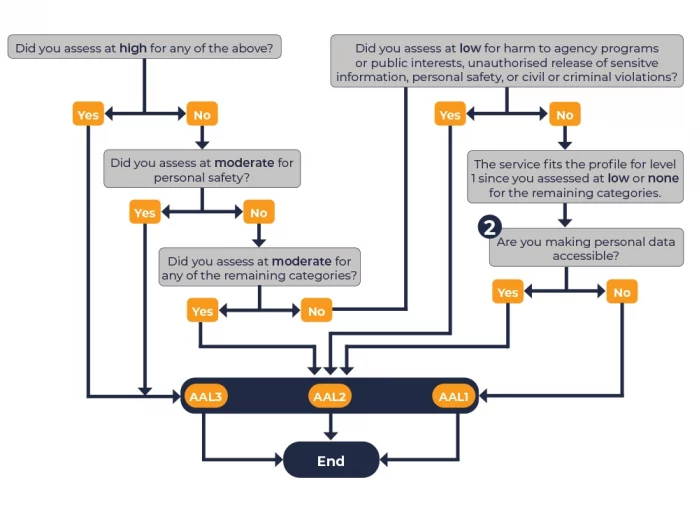
So how do you manage the risk and find out which level of assurance to use – our simple graphic above and flow chart below will help you understand which level of assurance you need to meet.
Authenticator Assurance Levels
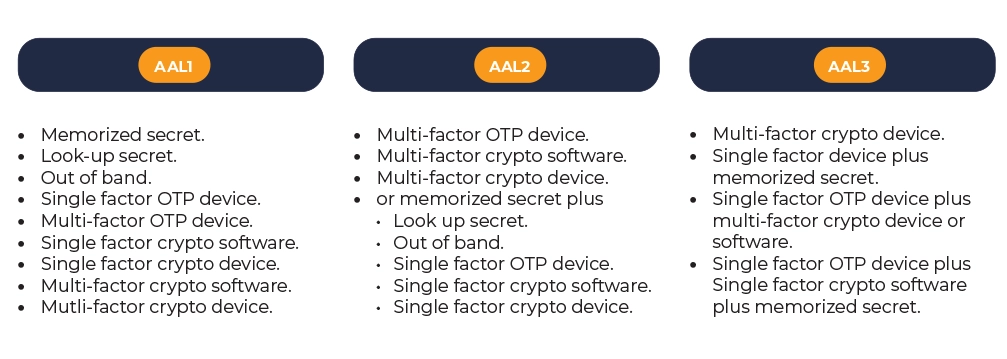
Within the category Authenticator Assurance levels, the standard has been split into levels, from AAL1 to AAL3, one being the least secure and 3 being very secure.
AAL1 – provides some assurance that the claimant controls an authenticator bound to the subscriber’s account.
AAL2 – provides high confidence that the claimant controls authenticator(s) bound to the subscriber’s account. Approved cryptographic techniques are required at AAL2 and above.
AAL3 – provides very high confidence that the claimant controls authenticators bound to the subscriber’s account. Authentication at AAL3 is based on proof of possession of a key through a cryptographic protocol. AAL3 authentication shall use a hardware-based authenticator. Approved cryptographic techniques are required such as PKI and FIDO2 authenticators.
Permitted Authenticator Types
The range of authenticators that can now be used within the FIPS201-3 standards has expanded. However, you need to be cautious – some manufacturers have devices that are capable of PKI and FIDO, but this may not be using the FIPS approved firmware in that device.
MyID® is a credential management system and enables organisations to do a lot of this out of the box in our standard product. MyID easily integrates with other IT systems in place and offers a single pane of glass to be able to view and manage the status of any given credential. With auditing and reporting included as standard.
Identity proofing – we know whether it has been done by MyID or brought in by the IDMS and the strength of that identity.
MyID can act as a PKI and FIDO authenticator we support both in the single product.
MyID can also issue derived credentials using the various form factors of authentication which are now allowed in FIPS201-3.
MyID supports software and hardware authenticators. FIDO is gaining traction, with phones and other devices starting to natively act as a FIDO authenticator and smartcard vendors adding FIDO capabilities to smartcards and tokens, like YubiKeys.
Using the MyID issuance policy, helps you to confirm you are issuing AAL3 cryptographic PKI or FIDO Authenticators. MyID makes sure that that device meets those criteria before it is provided for use.
MyID doesn’t just issue the credential to the device, but as the credential is bound to a person, you can view and manage the status of all your issued digital credentials, which devices they have been issued with and a view of derived credentials. MyID offers fully auditable reports, visibility to see who authorised what and when, giving you the ability to effectively manage your digital identities and credentials through one pane of glass, quickly, easily and in one place – fully enabling you to manage devices and credentials, easily through one system.
If you want to find out more, contact us today.
Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you
will find Intercede. Whether its citizen
data, aerospace and defence systems, high-value financial transactions,
intellectual property or air traffic control, we are proud that many leading
organisations around the world choose Intercede solutions to protect themselves
against data breach, comply with regulations and ensure business continuity.