The importance of strong workforce authentication for HIPAA
Healthcare has the unenviable tag of being the most heavily targeted sector by cybercriminals1 and so the Department of Health and Human services’ (HHS) Office for Civil Rights (OCR) are increasingly penalising healthcare providers who fail to show compliance to the Health Information and Portability Accountability Act (HIPAA).
Patient data is a valuable commodity on the dark web and breached data sells for large sums. The lack of control healthcare providers have once data is breached is a major concern for HHS. Unlike credit cards and bank accounts, which can be cancelled and closed, healthcare data is practically impossible to control once hacked and can be used by criminals for a variety of fraudulent activity.
HIPAA sets the standard for securing patient data for healthcare providers. Organisations that deal with protected healthcare information (PHI) must have physical, network and process security measures in place, and follow them to ensure HIPAA compliance.
PHI incorporates any data which identifies an individual and determines appropriate care – demographic information, insurance information, medical history, test and laboratory results.
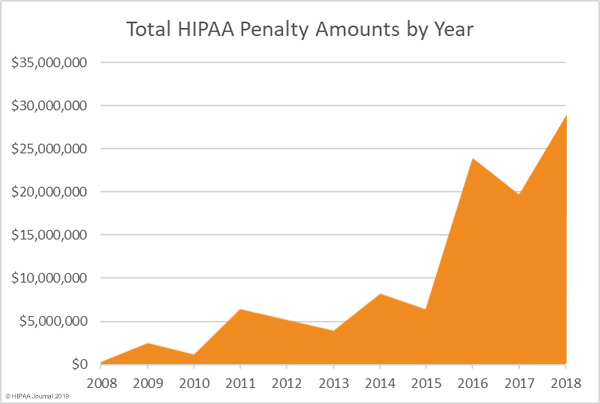
OCR clamping down on HIPAA non-compliance
In 2018 the OCR issued a record level of fines to healthcare providers who were found to not comply with HIPAA regulations. As the graph below highlights, fines reached a record $28.7m in 2018 with no signs of abating as data breach concerns continue to increase in 2019.
One point highlighted in 2018’s OCR fines is that the threat to healthcare providers doesn’t stop at cybercriminals. The largest fine levied at an organisation, Anthem Inc. stemmed from an attack which has later been found to be the responsibility of a nation-state hacker. Investigators haven’t named the country responsible, nonetheless Anthem Inc. were still hit with a $16m fine from the OCR for the hack in which 79m user records were breached.
Digital transformation and HIPAA compliance
Whether adopting a Computerized Physician Order Entry (CPOE) system, electronic health records (EHR), laboratory, radiology, or pharmacy systems, healthcare providers are embracing digital transformation.
Improving efficiency, data mobility and delivering better healthcare services are the drivers behind healthcare digital transformation and recent research shows that organisations are universally pushing ahead with transformation programs in some form.
When it comes to HIPAA compliance a concern with digital transformation is that it significantly increases the digital surface area at which healthcare providers are at risk of various hacking attempts.
Ensuring digital transformation is HIPAA compliant
HIPAA broadly comprises of four core regulatory rules:
- Privacy Rule
- Security Rule
- Breach Notification Rule
- Enforcement Rule
The HIPAA privacy and security rules are focused on safeguarding patient PHI whilst the breach and enforcement rules concern what happens when compliance isn’t met.
- HIPAA Privacy Rule: Requires appropriate safeguards to be in place to protect the privacy of PHI. To comply with the privacy rule, healthcare providers must consider how their processes ensure the confidentiality, integrity and availability of PHI meet HIPAA regulations. The privacy rule concerns all forms of PHI – paper, oral and electronic.
- HIPAA Security Rule: The security rule sets out the technical elements and safeguards that healthcare providers must put in place to secure patients’ electronic PHI (ePHI). A national security standard for healthcare information that is stored and accessed in an electronic form. In total there are 18 standards and 36 implementation specifications for organisations to meet.The aim of ePHI is to provide a robust set of standards that protects individuals’ health information whilst also allowing healthcare providers to adopt new technologies that improve the quality and efficiency of patient care delivery. Unlike a set of rigid standards, HIPAA regulations are in place to adapt to a healthcare provider’s size, organisational structure and the risks posed to the patient ePHI it’s responsible for.In summary, compliance to the HIPAA security rule involves:
- Ensuring the confidentiality, integrity, and availability of all ePHI that’s created, received, maintained and transmitted
- Identifying and protecting against reasonably anticipated threats to the security and/or integrity of information
- Protecting against reasonably anticipated, impermissible uses or disclosures
- Ensuring workforce compliance
The role of strong workforce authentication for HIPAA compliance
With employee related hacks increasing by more than a third2 and weak/stolen passwords being the cause of more than 8 in 10 data breaches in 20183, secure employee authentication is integral to ensuring HIPAA compliance to all four security rule elements.
Strong authentication for healthcare employees means providing a user-friendly means for workers, whether head office-based or remote, to prove their identity before accessing ePHI.
The best practice method of delivering strong workforce authentication is to adopt cryptographic two-factor authentication (2FA) using public key infrastructure (PKI).
Through a PKI system, managed by a credential management system like Intercede’s MyID®, healthcare providers are able to issue cryptographically protected credentials to employees across a variety of devices.
Whether it’s a HR Advisor logging in to their head office PC and accessing on-premise HR systems, or a field practitioner accessing ePHI data in the cloud via their laptop or tablet, MyID enables cryptographically protected credentials to be issued down to a variety of technologies.
Once a credential is issued a healthcare worker can authenticate using a PIN or biometric data to login and access ePHI.
The multi-factor element of the solution stems from the fact that only a user with the correct credentialled device (something I have), plus correct PIN (something I know) or biometric (something I am) can access ePHI information. A solution that removes the threat of data breach through phishing, credential stuffing and other password/account takeover attempts.
“We are working with a number of US healthcare providers who are adopting strong authentication for HIPAA compliance and to protect ePHI from data breach.
“Our MyID product is widely used in government, aerospace, and defense organisations but we are seeing a growing demand in the healthcare space for a more secure means of allowing employees to authenticate. PKI credentials, issued and managed by MyID delivers just that.” Says Allen Storey, Chief Product Officer at Intercede.
You can discover more about MyID for healthcare providers here or contact us now via the form below to discuss your requirements further.
References
- Thales Data Threat Report 2019; https://www.thalesesecurity.com/2019/data-threat-report-healthcare
- IBM X-Force Threat Intelligence Index 2018; https://www.ibm.com/uk-en/security/xforce
- Verizon Data Breach Investigations Report 2018; https://enterprise.verizon.com/resources/reports/DBIR_2018_Report_execsummary.pdf
Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you
will find Intercede. Whether its citizen
data, aerospace and defence systems, high-value financial transactions,
intellectual property or air traffic control, we are proud that many leading
organisations around the world choose Intercede solutions to protect themselves
against data breach, comply with regulations and ensure business continuity.