REGISTRATION AND IDENTITY VERIFICATION
Verify user identities prior to credential issuance, compliant with NIST FIPS-201.
Enrollment, and the process of verifying each person are who they claim to be, is essential for all digital identity deployments but this isn’t always as simple as it should be. MyID IDV (an optional add-on to the MyID PIV CMS product) provides all of the processes and integration required to register, verify and approve individuals are who they claim to be prior to issuing them with a credential.
Key MyID capabilities include:
- Onboarding of individuals to start the registration process
- Flexible applicant data capture, including biographic, biometrics, and document scans and ID document validation.
- Integration with 1:N biometric uniqueness checking solutions to prevent fraudulent re-enrollment
- Integration with background checking solutions
- ID verification prior to approving credential checking solutions.
ROBUST DIGITAL IDENTITY VERIFICATION AND ISSUANCE IN ONE PLACE
By combining credential management with registration and identity proofing, MyID enables organisations to ensure that identities are verified before credentials are issued and comply with NIST FIPS 201 security regulations.
DEVICE FLEXIBILITY
By incorporating world leading biometric components from Aware into the MyID registration and verification workflows, MyID provides a high degree of independence from the biometric devices used for fingerprint and facial capture. This enables organisations to maintain flexibility when choosing hardware capture devices and often allows them to support the devices they already have deployed.

HOW IT WORKS
Sponsorship
MyID can be provided with initial sponsorship data (the basic person data required to begin the registration process) by a number of mechanisms, which can be used concurrently if required:
- LDAP – data is retrieved from an LDAP directory
- API – data is passed in to MyID from a 3rd party system via APIs
- Operator entry – data can be entered directly into MyID by an authorised operator
The data captured is highly configurable and can easily be altered to meet the requirements of a particular organisation or standard.
Identity Verification
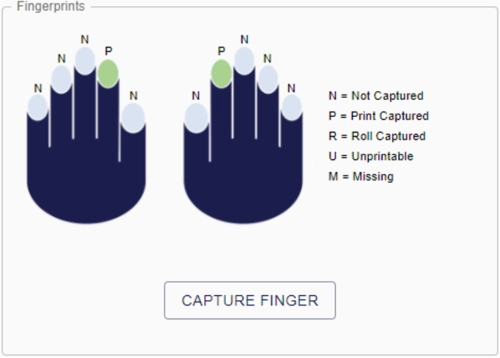
Identity verification is the process of verifying an applicant’s data against a 1:many biometric matching system and/or 3rd party watchlists, often includes a combination of automated system responses and human review/approval, capabilities include:
- Integration with ABIS (Automated Biometric Identification System) solutions to provide 1:N fingerprint matching.
- APIs for passing and receiving responses from background checking solutions.
- Adjudication workflows within MyID to escalate exceptions or approve requests for credentials.
Policy, Governance and Monitoring
At the heart of the MyID system is a backend web server / app server / database platform that puts organisations in full control of the identities they register and credentials they manage. Providing flexible policy settings, configuration settings and security options, including:
- Role separation – control over who can sponsor, who can register and who can verify, including enforcement of the ‘two pairs of eyes’ principle, ensuring a single bad actor cannot create fraudulent credentials.
- Flexible data capture, controlling what attributes are captured at which stage and who has access to them.
- Audit – central signed audit trail for all MyID operations, provides non-repudiation and investigative capabilities.
- Reporting – MyID operations are available via built in enquiries, reports and APIs for integration into business intelligence tools.
- Monitoring – APIs and SNMP support for monitoring system availability and status.
Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you will find Intercede. Whether its citizen data, aerospace and defense systems, high-value financial transactions, intellectual property or air traffic control, we are proud that many leading organizations around the world choose Intercede solutions to protect themselves against data breach, comply with regulations and ensure business continuity.


