STRONG MOBILE AUTHENTICATION
The MyID product family enables mobile devices to be used for strong authentication across a range wide range of authentication technologies.
MyID MFA support use of mobile devices for authentication via:
- Sending OTP message over SMS
- Generating OTP codes via an App
- Push notification, including MFA fatigue protection and context based information
- Use of a Mobile device as a syncable FIDO passkey for phishing-resistant authentication
MyID CMS support use of mobile devices for authentication via:
- PKI based authentication for those requiring certificate based authentication or transaction signing
MyID turns your workforce’s mobile phones into strong authentication devices, enabling passwordless multi-factor authentication for end users into cloud resources, corporate systems and networks through touch ID, facial biometric or a PIN.
Simple to deploy, MyID plugs into existing environments, and provides all of the management necessary for IT teams to control access policies, issue, and manage the lifecycle of end user credentials on mobile -devices.
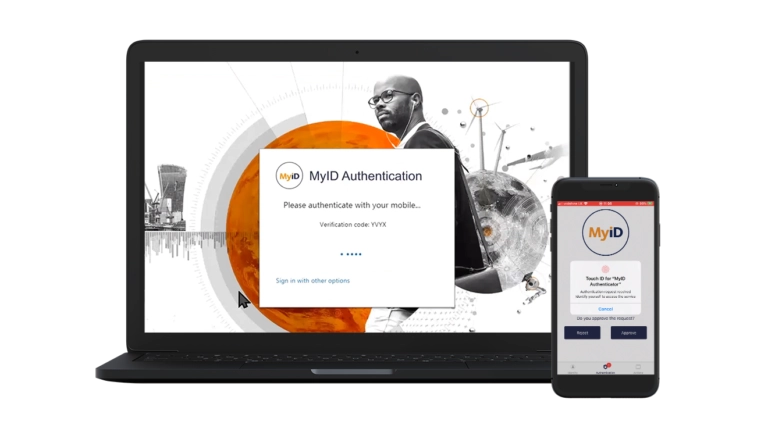
USE STRONG MOBILE AUTHENTICATION TO
- Reduce hardware costs by enabling end users’ mobile devices for strong authentication.
- Provide best practice strong multi-factor authentication to safeguard against the growing threat of data breach from weaker forms of authentication.
- Deliver strong authentication with an excellent user experience using in-built device touch ID, PIN or FaceID technology.
- Remove deployment headaches by working with existing infrastructure.
- Maintain centralized control over the digital credentials issued, policies set in place and lifecycle management of mobile credentials.
WATCH THE VIDEO
THE BENEFITS OF MOBILE AUTHENTICATION WITH MyID
Want to know more?
If you are ready to book a demo, simply click the button below and we will arrange a demo
demo requestTrusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you will find Intercede. Whether its citizen data, aerospace and defense systems, high-value financial transactions, intellectual property or air traffic control, we are proud that many leading organizations around the world choose Intercede solutions to protect themselves against data breach, comply with regulations and ensure business continuity.


