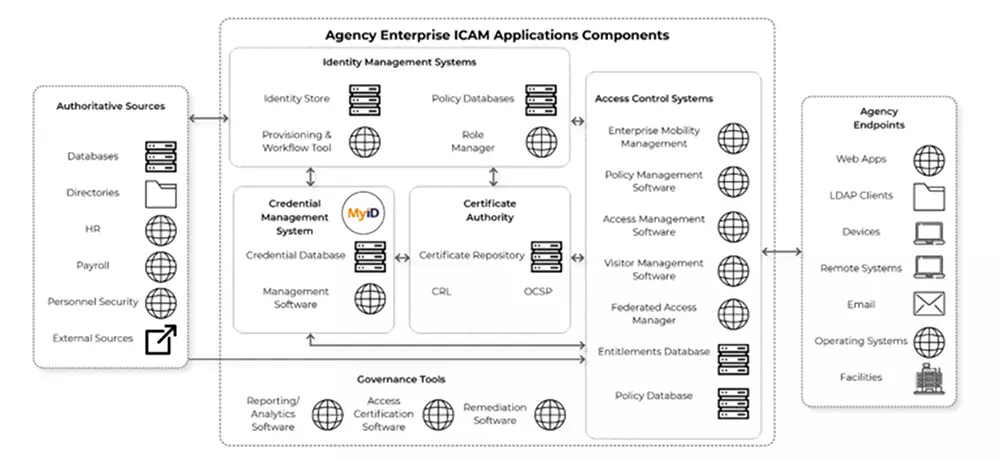
PROVIDING A BEST PRACTICE FRAMEWORK FOR DERIVED PERSONAL IDENTITY VERIFICATION (PIV) CREDENTIALS
The National Institute of Standards and Technology’s (NIST) National Cybersecurity Center of Excellence (NCCoE) are the United States’ leading body in providing real world, best practice architectures for federal agencies and companies to overcome specific cybersecurity challenges.
THE BENEFITS
Trusted by Governments and Enterprises Worldwide
Where protecting systems and information really matters, you will find Intercede. Whether its citizen data, aerospace and defense systems, high-value financial transactions, intellectual property or air traffic control, we are proud that many leading organizations around the world choose Intercede solutions to protect themselves against data breach, comply with regulations and ensure business continuity.